Understanding Carding: A Comprehensive Guide for Online Store Owners
Carding is a type of credit card fraud that happens when a carder (or credit card thief) uses a stolen card to purchase branded gift cards, buy high-value goods, or charge a prepaid card. It is also called credit card stuffing.
Sadly, the US is a major target for carding since it doesn’t employ chip and PIN technology similar to what other countries use to safeguard debit and credit cardholders. In fact, between 2020 and 2021, card fraud increased by over 10% worldwide, with US merchants and card owners alone losing $12 billion. It is expected to cause losses of over $362 billion to global merchants between 2023 and 2028.
In this article, you’ll learn about how carding fraud attacks work, the top carding attack techniques used today, and the measures to take to combat it.
Let’s get started.
How a carding attack works
A carding attack is a major e-commerce security threat usually executed online through a merchant’s payment processor. A cybercriminal will hack into the merchant’s online credit card processor and get a list of all debit and credit cards most recently used.
That’s not to say that’s the only way they can gain access to credit card information (we’ll discuss these other strategies in the next section). Suffice it to say that however they retrieve the credit card data, they use a bot—software made for performing automated tasks over the internet—to determine if the credit card details are valid.
Once a card is proven to be valid, it is used for even more illegal activities. For example, it can be used to buy store-branded gift cards, which will then be used to buy products from the store to be sold for cash. These unscrupulous individuals can even choose to sell these prepaid gift cards themselves. Some carders go as far as selling all the verified card details to criminal rings on carding forums and other criminal markets. In fact, in 2022, credit card data on the dark web skyrocketed by a whopping 135%.
Unfortunately, the original card owner mostly remains unaware of this until all their funds have been used or transferred. At this point, it’s usually too late to recover the money.
The thing is, carding is not only disadvantageous to the cardholder. It’s also detrimental to the merchant. Any time there’s a disputed purchase, the merchant may be forced to give chargebacks. This means they have to reverse the online purchases or transactions and refund the money to the cardholder’s account.
The merchant may also face additional financial burden in the form of carding reversal charges as part of their service agreements. They may also lose money from legitimate online purchases if payment processors decide to block transactions until the issue is resolved. Recovering the products carders purchase is also hard. Then, of course, there’s the reputational damage that’s even harder to repair.
What are the top carding attack techniques?
We’ve briefly touched on how hackers can gain access to payment card data for their carding attacks. In this section, let’s look in detail at other techniques:
Credit Card Skimming
Credit card skimming occurs when criminals alter an ATM machine, gas pump, or POS system with a similar-looking piece of equipment. This equipment then records the magnetic strip code, card number, expiration date, and PIN.
The criminals will then use Bluetooth to transfer card information to their own devices, hardly ever coming into contact with the original machine.
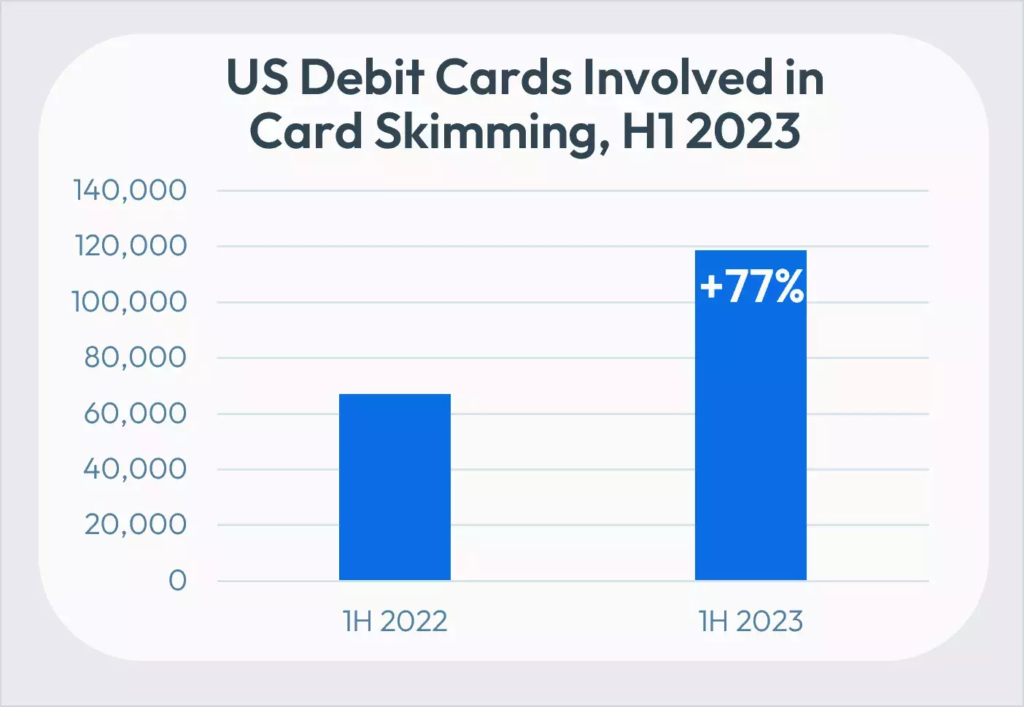
In the first half of 2023 alone, 120,000 cards and 3,000 unique financial institutions were affected by card skimming attacks. This was a staggering 77% increase in skimming incidents from the previous year.
Social Engineering
Social engineering refers to the practice of manipulating a person to divulge confidential information–including credit card details—to be used for criminal purposes. The information can also be used to gain access to the victim’s computer system and steal other sensitive data like social security numbers.
Phishing, vishing, smishing and pharming are types of social engineering attacks.
A phishing scam happens when cyber criminals send emails to unsuspecting people while purporting to be from known companies. These emails attempt to induce the victim to divulge sensitive information such as bank account info, credit card details, usernames, or passwords.
Vishing and smishing are similar to phishing. Only, vishing involves the use of phone calls to gain access to a person’s sensitive information. Smishing, meanwhile, involves the use of SMS. A malicious link is typically included in the SMS. When the unsuspecting victim clicks on the link, they are directed to a website, which may prompt them to download malicious software. We’ll talk about malware later.
The last one, pharming, involves redirecting website traffic to another fake site, which then prompts the victim to disclose critical information.
Social engineering accounts for a whopping 98% of cyber-attacks. According to the FBI’s Internet Crimes Unit, in 2021, phishing, vishing, smishing and pharming victims amounted to 323972, the most number of cybersecurity victims.
Malware
Malware refers to intrusive or malicious software created by hackers to damage computer systems or gain unauthorized access to them. Trojan viruses, worms, ransomware, spyware, viruses, and adware are all examples of malware.
The majority of malware is spread as trojan viruses like .doc files and .exe files, and can be distributed using some form of social engineering. The number of malware attacks is increasing by the year. In fact, in 2022, there were 5.5 billion malware attacks, a 2% rise from the previous year.
As you’ve seen, cybercriminals may employ a combination of the tactics above to gain access to credit card details they’ll use for a carding attack. That’s why for the best protection, cardholders should take the time to understand these strategies and implement cybersecurity best practices to prevent or counter them. For instance, they shouldn’t click on dubious links. They should also take the time to check the authenticity credit protection servicesof the messages sent to them. Another option is to use credit protection services that can alert them of fraudulent activities related to their card.
eCommerce businesses like you should do their part as well. They should identify all points of vulnerability in their site hackers may exploit to get a hold of sensitive information, including customers’ credit card details. They may use AI chatbots for hacking purposes to identify these. Once identified, they can make the necessary adjustments or deploy the appropriate cybersecurity solutions.
What are the measures implemented by businesses to combat carding fraud
As criminals get better at scheming, businesses are forced to get better at data protection. That said, let’s look at a few other measures used by businesses to combat carding fraud, and which you can implement, too.
1. Address verification service (AVS)
The AVS system compares the billing address provided at checkout to the one in the card issuer’s records. The result can be one of these three:
- Full match
- ZIP code match
- Address match
- No match
If the details do not match, the transaction is considered criminal activity and will be declined immediately. Sometimes, the AVS system leaves it to the discretion of the merchant to choose whether or not to decline a partial match.
Unfortunately, AVS only works in the US, Canada, Australia, New Zealand, and the UK.
2. Card verification value (CVV) checks
CVV is a three or four-digit code written on the back of a credit or debit card, close to the signature strip.

You can request this unique code upon checkout to verify that the shopper who wishes to make a purchase is in physical possession of the card. This will make it impossible for carders to use credit card numbers retrieved from criminal marketplaces or the Dark Web for fraudulent activities.
3. Geolocation tracking
Geolocation tracking leverages GPS technology to identify the user’s location or IP address and compare it to the one that’s normally used and was initially registered by the cardholder. Some advanced geolocation tracking systems can check for device type, transaction history, and even time of day.
Geotrackers can also identify users who are accessing a site using proxy IPs. Proxy IPs help users show they’re accessing a site from one location when they’re actually in an entirely different one.
While it’s possible the real cardholder could simply be traveling, a geolocation mismatch shouldn’t be overlooked. You should conduct more tests–maybe ask questions only the legitimate cardholder would know—to ensure the card details are in the right hands.
4. CAPTCHA
CAPTCHA is an online security test used to ward off bots by trying to verify that the website user is a human. CAPTCHA is short for Completely Automated Public Turing test to tell Computers and Humans Apart. It uses a challenge-response framework.
For instance, a CAPTCHA can display several similar images and ask the user to select those with a bicycle, fire hydrant, motorcycle, or other objects. Below is an example of a CAPTCHA test.

While humans can find this easy, bots find it extremely challenging and almost impossible. It’s an effective way to prevent password decryption by AI bots and protect your e-commerce store.
To implement CAPTCHA on your site, all you need to do is register your site on the Google reCAPTCHA website.
Apart from all these measures, the business can also opt to invest in the cybersecurity education of their IT and security teams. Gaining a cybersecurity certification can help in responding effectively during any carding fraud incidents.
In closing
Carding fraud is a growing challenge that needs to be addressed. This type of fraud happens when a carder (or credit card thief) gets a hold of a user’s credit card details, uses bots to verify the details are valid, then uses the card for illegal activities.
As an eCommerce business, you need to guard against these attacks. Implement one or more of these measures—Address Verification Services (AVS), Card Verification Value checks (CVV), geolocation tracking, and CAPTCHA. You might also want to consider AVS, but that’s only available in a few countries.
With the right security measures, you won’t only protect your online store. You’ll also keep your customer data safe and, ultimately, build trust and credibility that are crucial to business growth.

About the author:
Dillon Deckard is a seasoned content writer at StationX with over seven years of experience in the field of cybersecurity. He has a knack for finding fresh ideas and is always eager to learn new things. He is passionate about sharing actionable insights through his approachable blog posts, which are designed to empower marketers at all levels. You can find him on LinkedIn, where he is always open to networking and connecting with professionals in the industry.
Yan Anderson is the Head of Content Marketing at CS-Cart with over 10 years of experience in the eCommerce industry. He's passionate about explaining complicated things in simple terms. Yan has expertise in building, running and growing eCommerce marketplaces. He loves to educate people about best practices, new technologies, and trends in the global eCommerce industry.

